Managing the watsonx.ai Runtime service endpoint
You can use IBM Cloud connectivity options for accessing cloud services securely by using service endpoints. When you provision a watsonx.ai Runtime service instance, you can choose if you want to access your service through the public internet, which is the default setting, or over the IBM Cloud private network.
How you access service endpoints depends on the Cloud platform you are using.
Accessing endpoints on IBM Cloud
You can use the Service provisioning page to choose a default endpoint from the following options:
- Public network
- Private network
- Both, public and private networks
For more information, refer to IBM Cloud service endpoints.
Public network
You can use public network endpoints to connect to watsonx.ai Runtime service instance on the public network. Your environment needs to have internet access to connect.
Private network
You can use private network endpoints to connect to your IBM watsonx.ai Runtime service instance over the IBM Cloud Private network. After you configure your watsonx.ai Runtime service to use private endpoints, the service is not accessible from the public internet.
Private URLs for watsonx.ai Runtime
Private URLs for watsonx.ai Runtime for each region are as follows:
- Dallas - https://private.us-south.ml.cloud.ibm.com
- London - https://private.eu-gb.ml.cloud.ibm.com
- Frankfurt - https://private.eu-de.ml.cloud.ibm.com
- Tokyo - https://private.jp-tok.ml.cloud.ibm.com
Using IBM Cloud service to enable private endpoints
Follow these steps to enable private network endpoints on your clusters:
- Use IBM Cloud CLI to enable your account to use IBM Cloud service endpoints.
- Provision a watsonx.ai Runtime service instance with private endpoints.
Provisioning with service endpoints (Dallas, Frankfurt, Tokyo, London)
You can provision a watsonx.ai Runtime service instance with service endpoint by using IBM Cloud UI or IBM Cloud CLI.
Provisioning a service endpoint with IBM Cloud UI
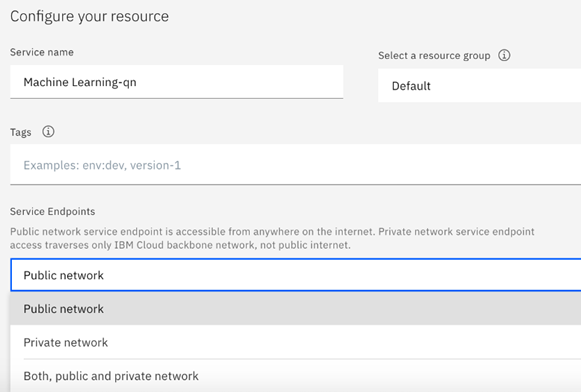
To configure the endpoints of your IBM watsonx.ai Runtime service instance, you can use the Endpoints field on the IBM Cloud catalog page. You can configure a public, private, or a mixed network.
IBM Cloud CLI
If you provision an IBM watsonx.ai Runtime service instance by using the IBM Cloud CLI, use the command-line option service-endpoints to configure the watsonx.ai Runtime endpoints. You can specify the value publicprivatepublic-and-private
ibmcloud resource service-instance-create <service instance name> pm-20 <plan_name> <region> --service-endpoints <private/public/public-and-private>
For example:
ibmcloud resource service-instance-create wml-instance pm-20 standard us-south -p --service-endpoints private
or
ibmcloud resource service-instance-create wml-instance pm-20 standard us-south --service-endpoints public-and-private
Provisioning a service endpoint (Sydney and Toronto)
To provision a service endpoint for a watsonx.ai Runtime instance in either the Sydney or Toronto region, you must request access to a Private Catalog. After the request is approved, you can share the endpoint as a Virtual Private Endpoint.
Requesting access to a private catalog
To request access to a Private Catalog, follow these steps:
- Use IBM Cloud CLI to enable your account to use IBM Cloud service endpoints.
- Contact IBM Support and submit a request, asking the watsonx.ai Runtime team provide you with access to a Private Catalog. You must supply your IBM Cloud accountID with the request.
- When the watsonx.ai Runtime team provides access to the Private Catalog to customers account ID, you can view the completed request and catalog details from Manage>Catalogs>Share requests in the IBM Cloud console. You can then create a virtual private endpoint gateway.
- Select Virtual Provate Endpoint as the catalog type. For example:

- Follow the steps to create a Virtual private endpoint gateways for VPC. Use the following as the Private Catalog display names for the Sydney and Toronto data
centers:
- SYDNEY : mcsp-wml-sydprod
- TORONTO : mcsp-wml-torprod
Verifying approval
To verify that the customer has accepted the share request, use the following command:
ibmcloud catalog account get-approval-list-source --object-kind vpe --approval-state approved
{
"first": "/api/v1-beta/shareapproval/vpe/access/source/approved?limit=100",
"limit": 100,
"resource_count": 1,
"resources": [
{
"_id": "<account id>",
"_rev": "2-93907d1b7d449c1a82914dfde604f316",
"account": "fc3acf288b1b451e8cb981b2b9423b14",
"account_type": 3,
"created": "2025-02-26T01:15:21.513749288-05:00",
"id": "<account id>",
"target_account": "ba083c5877a64197a36b55d259812dfa",
"target_kind": "vpe"
}
]
}
This command returns a list of approved requests, including the account ID and target account ID.
Accessing private endpoints from AWS
To access private endpoints from AWS you use a Service Distributed Network Load Balancer (SDNLB) to set up a and manage a Virtual Private Endpoint (VPE). After creating a service ID and specifying an allow list, you create a catalog on the IBM Cloud console for listing and sharing private endpoints.
-
Follow the steps in Creating and working with service IDs to create a service ID for your SDNLB.
-
Create an allow list for the ServiceID by providing the following information to
ibmcloud-service-dnlbService name: MCSP-Production Service contact name and email: (Name, email@*.ibm.com) Service account name: (Account where this service is needed)CloudRock Production's Account Service account ID: xxx (Account ID) Service ID: sdnlb-mcsp-prod (ServiceId-xxxx) Env: production (cloud.ibm.com)or (test.cloud.ibm.com) -
Create an APIKey for the serviceID and grant access, as follows:
VPC Infrastructure Services All Editor Resource group only Default resource group Viewer All Account Management services All Viewer Resource group only CloudRock resource group Viewer Catalog Management All Viewer, Editor, Publisher -
Create a private catalog object, as follows:
{ "dns_domain": "private.au-syd.ml.cloud.ibm.com", "endpoint_type": "vpe", "fully_qualified_domain_names": [ "private.au-syd.ml.cloud.ibm.com" ], "service_crn": "crn:v1:bluemix:public:mcsp-wml-sydprod:au-syd:::endpoint:private.au-syd.ml.cloud.ibm.com" } -
Create the secret cluster for the SDN in the
kube-systemsdnlb-configkube-systemsdnlb.toml./sdnlb.tomlaccount_id = "user@xx.xxx.com" service_id = "service-account-ID" service_apikey = "service-account-apiKey" kubectl create secret generic -n kube-system sdnlb-config --from-file ./sdnlb.toml -
Create the LoadBalancer for each specific deployment, following the steps in Example 1: Single port SDNLB. For example, this configuration file shows a loadbalancer set up to access a server in a Sydney data center.
create SDNLB service apiVersion: v1 kind: Service metadata: labels: app: router type: sdnlb name: private-ingress-sdnlb-mcspsydprod namespace: openshift-ingress annotations: service.kubernetes.io/ibm-load-balancer-cloud-provider-enable-features: "service-dnlb" service.kubernetes.io/ibm-load-balancer-cloud-provider-ip-type: "private" service.kubernetes.io/ibm-load-balancer-cloud-provider-vpc-service-crn: "crn:v1:bluemix:public:mcsp-wml-sydprod:au-syd:::endpoint:private.au-syd.ml.cloud.ibm.com" spec: type: LoadBalancer selector: ingresscontroller.operator.openshift.io/deployment-ingresscontroller: default ports: - name: http port: 80 - name: https port: 443 -
Use this command to check if the NodePort specified in the previous step is available.
kubectl describe service private-ingress-sdnlb -n openshift-ingressIf the NodePort is not available, use this command to open the port:
kubectl get service private-ingress-sdnlb -n openshift-ingress –o wide -
Create the service for a private endpoint. For example:
apiVersion: v1 kind: Service metadata: name: wmlproxyserviceprivateonly namespace: swml-prod-default spec: ports: - port: 443 targetPort: 8443 selector: app: wmlproxyprod type: ClusterIP -
Create a route based off
wmlproxyserviceprivateonlyoc create route passthrough --service wmlproxyserviceprivateonly --hostname private.au-syd.ml.cloud.ibm.com -n swml-prod-default -
Create a VPE Gateway on the watsonx.ai Runtime cluster resource group. For example:

-
After you create the VPE, confirm that the private endpoints are working from the cluster. Open a pod and access the private endpoint, as follows:
[wmluser@wmlproxyprod-85bd985475-g564h /]$ curl -k https://private.au-syd.ml.cloud.ibm.com/heartbeat {"message": "Proxy is running!"}
Parent topic: Deploying and managing AI assets