About cookies on this site Our websites require some cookies to function properly (required). In addition, other cookies may be used with your consent to analyze site usage, improve the user experience and for advertising. For more information, please review your options. By visiting our website, you agree to our processing of information as described in IBM’sprivacy statement. To provide a smooth navigation, your cookie preferences will be shared across the IBM web domains listed here.
Last updated: Nov 27, 2024
Inbound firewall access allows Cloud Pak for Data as a Service to connect to Redshift on AWS through the firewall. You need inbound firewall access to work with your data stored in Redshift.
To connect to Redshift from Cloud Pak for Data as a Service, you configure inbound access through the Redshift firewall by entering the IP ranges for Cloud Pak for Data as a Service into the inbound firewall rules (also called ingress rules). Inbound access through the firewall is configurable if Redshift resides on a public subnet. If Redshift resides on a private subnet, then no access is possible.
Follow these steps to configure inbound firewall access to AWS Redshift:
-
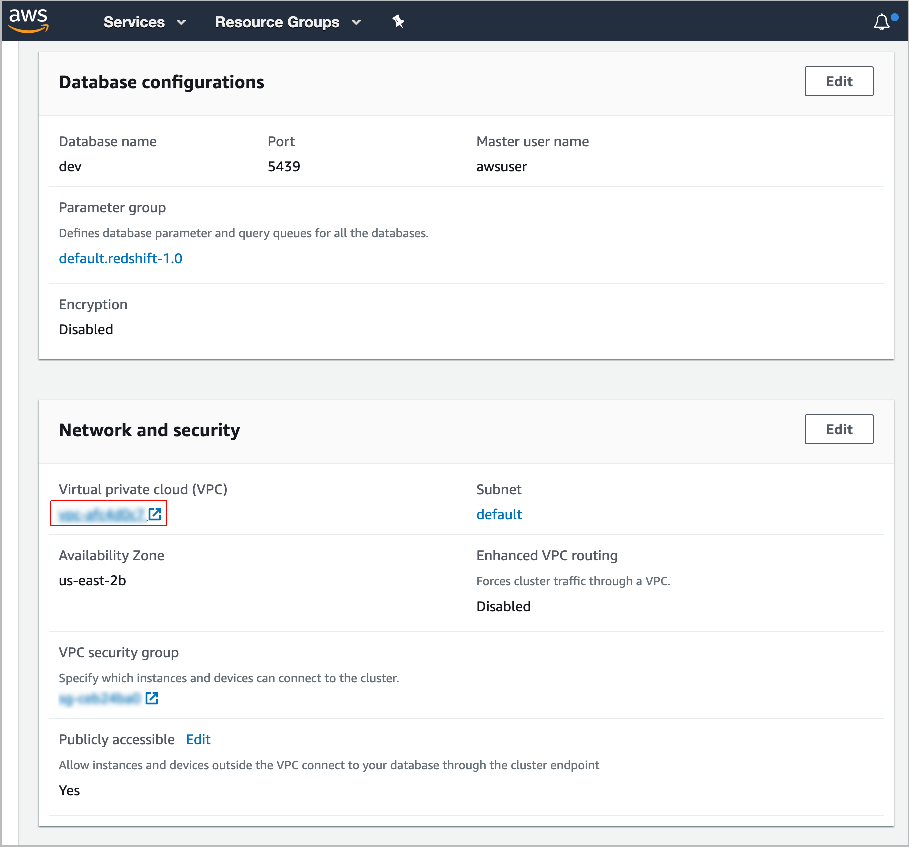
Go to your provisioned Amazon Redshift cluster.
-
Select Properties and then scroll down to Network and security settings.
-
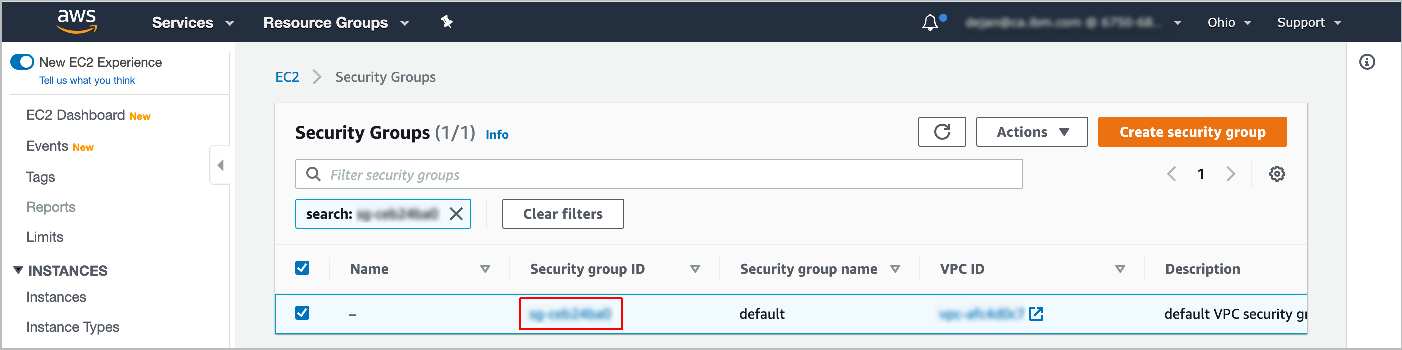
Click the VPC security group.
-
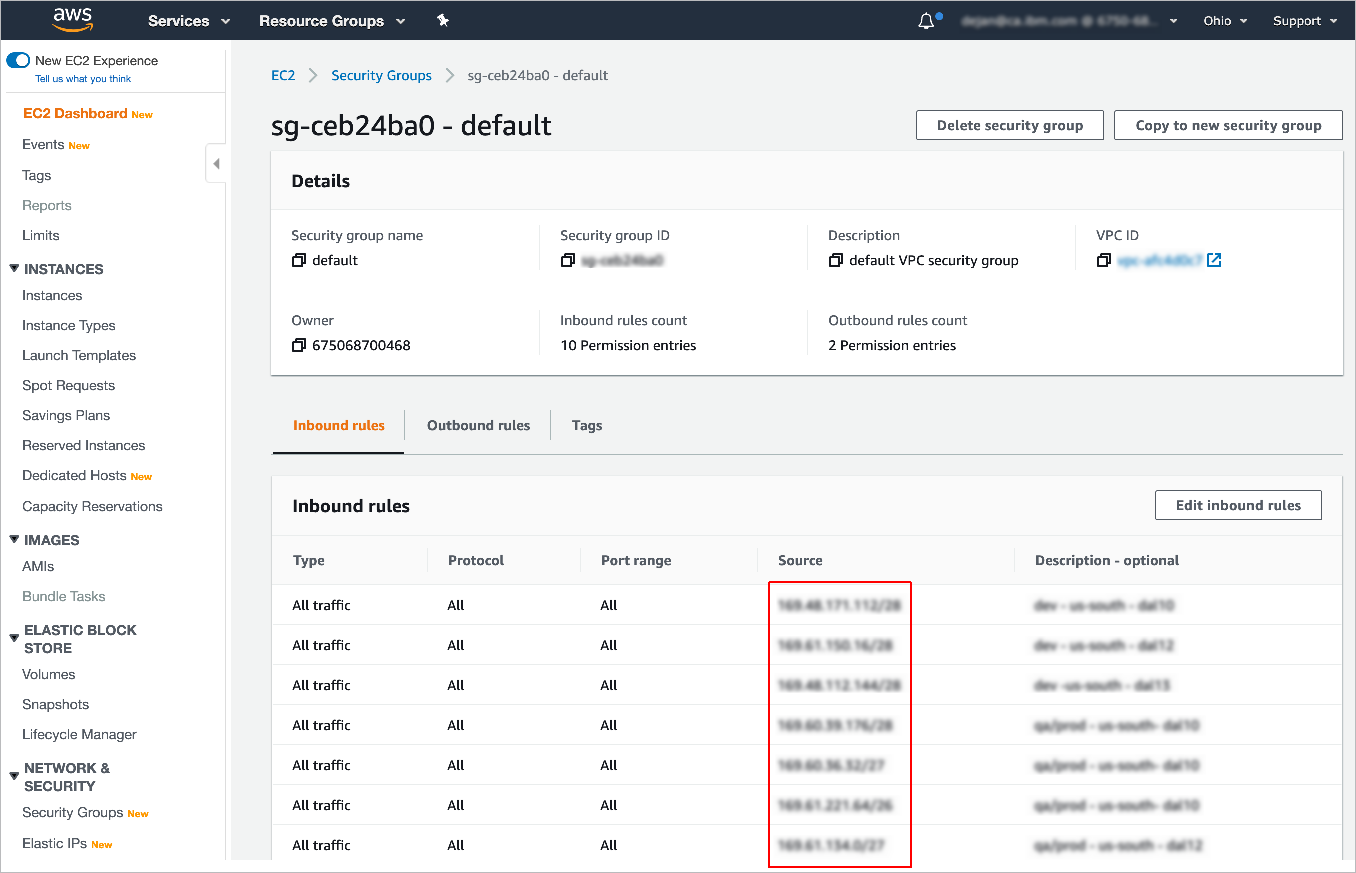
Edit the active/default security group.
-
Under Inbound rules, change the port range to 5439 to specify the Redshift port. Then select Edit inbound rules > Add rule.
-
From Cloud Pak for Data as a Service, go to the Administration > Cloud integrations page.
-
Click the Firewall configuration link to view the list of IP ranges used by Cloud Pak for Data as a Service. IP addresses can be viewed in either CIDR notation or as Start and End addresses.
-
Copy each of the IP ranges listed and paste them into the Source field for inbound firewall rules.
Learn more
Parent topic: Configuring firewall access